环境 almalinux9.3
openssl版本 3.x
证书生成简化脚本
#!/bin/bash
# 1、生成私钥公钥,自己作为CA机构。
echo "#############################################################################################################"
echo "生成CA证书"
mkdir ca && cd ca
openssl genpkey -algorithm RSA -out ca.key -pkeyopt rsa_keygen_bits:2048
openssl req -new -key ca.key -out ca.csr
cat <<EOF > v3_ca.ext
basicConstraints = critical, CA:TRUE
keyUsage = critical, keyCertSign, cRLSign
subjectKeyIdentifier = hash
EOF
openssl x509 -req -in ca.csr -signkey ca.key -out ca.crt -days 3650 -extfile v3_ca.ext
# 注意这里明确声明自己作为CA,CA:TRUE。
echo "#############################################################################################################"
cd ..
# 给服务器(域名)颁发证书
echo "#############################################################################################################"
echo "生成域名证书"
mkdir server && cd server
openssl genpkey -algorithm RSA -out server.key -pkeyopt rsa_keygen_bits:2048
openssl req -new -key server.key -out server.csr
# 创建一个SAN文件
cat <<EOF > san.conf
authorityKeyIdentifier=keyid,issuer
basicConstraints=CA:FALSE
keyUsage = digitalSignature, keyEncipherment
extendedKeyUsage = serverAuth
subjectAltName = @alt_names
[alt_names]
DNS.1 = www.test.com
DNS.2 = test.x.com
IP.1 = 127.0.0.1
IP.1 = 192.168.6.114
EOF
# 用ca的证书给csr颁发证书
openssl x509 -req -in server.csr -CA ../ca/ca.crt -CAkey ../ca/ca.key -CAcreateserial -out server.crt -days 365 -extfile san.conf
# 验证证书链
echo "验证证书链"
openssl verify -CAfile ../ca/ca.crt server.crt
#如果输出 server.crt: OK,说明证书链正确。
echo "#############################################################################################################"
cd ..
echo "#############################################################################################################"
echo "生成客户端证书"
mkdir client && cd client
openssl genpkey -algorithm RSA -out client.key -pkeyopt rsa_keygen_bits:2048
openssl req -new -key client.key -out client.csr
openssl x509 -req -in client.csr -CA ../ca/ca.crt -CAkey ../ca/ca.key -CAcreateserial -out client.crt -days 365
echo "#############################################################################################################"
rm -f /home/software/openresty/nginx/conf/vhost/server/*
cp ../server/* /home/software/openresty/nginx/conf/vhost/server/
cp ../ca/ca.crt /home/software/openresty/nginx/conf/vhost/server/
/home/software/openresty/nginx/sbin/nginx -s reload
echo "curl访问"
curl --cert client.crt --key client.key --cacert ../ca/ca.crt https://www.test.com
# 为了将证书导入到浏览器,生成p12格式
openssl pkcs12 -export -inkey client.key -in client.crt -out client.p12 -name "ClientCert"
# nginx配置
server {
listen 80;
listen 443 ssl;
http2 on;
server_name www.test.com;
root /www;
index index.php index.html;
ssl_certificate /home/software/openresty/nginx/conf/vhost/server/server.crt;
ssl_certificate_key /home/software/openresty/nginx/conf/vhost/server/server.key;
ssl_session_timeout 5m;
ssl_protocols TLSv1.1 TLSv1.2;
ssl_ciphers ECDHE-RSA-AES128-GCM-SHA256:HIGH:!aNULL:!MD5:!RC4:!DHE;
ssl_prefer_server_ciphers on;
ssl_verify_client on;
ssl_client_certificate /home/software/openresty/nginx/conf/vhost/server/ca.crt;
client_max_body_size 100M;
server_tokens off;
fastcgi_hide_header X-Powered-By;
location ~ \.php$
{
fastcgi_split_path_info ^((?U).+.php)(/?.+)$;
fastcgi_param PATH_INFO $fastcgi_path_info;
fastcgi_param PATH_TRANSLATED $document_root$fastcgi_path_info;
fastcgi_pass 127.0.0.1:10000;
fastcgi_index index.php;
fastcgi_param SCRIPT_FILENAME $document_root$fastcgi_script_name;
fastcgi_param RGS_COREPATHNAME GameMotors;
include fastcgi_params;
}
access_log /var/log/nginx/www.test.com-access.log;
error_log /var/log/nginx/www.test.com-error.log;
}
# ssl_verify_client on 是开启验证客户端证书。
# ssl_client_certificate 这个参数告诉nginx我信任这个文件中的 CA,如果客户端提交的证书是由这些 CA 签发的,那我就接受。
1、首先双击 ca.crt 文件,导入到本地,选择 受信任的根证书颁发机构。这样浏览器才会信任,不会报不安全。
2、Chrome浏览器导入p12证书,点击 设置 – 隐私与安全 – 安全 – 管理证书 – 您的证书 – 管理从Windows导入的证书
点击 导入,选择刚才的p12证书文件。 “证书存储” 部分,选择 “将所有的证书都放入下列存储”,选择 “个人” ,完成。
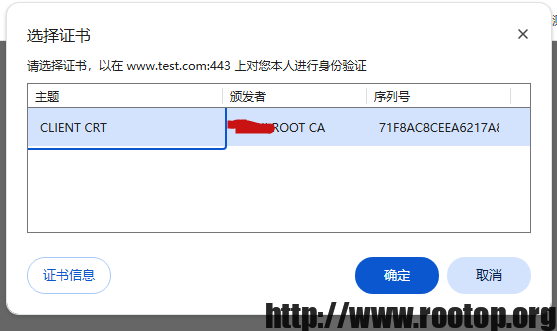
浏览器访问 https://www.test.com/ 会弹窗选择客户端证书。
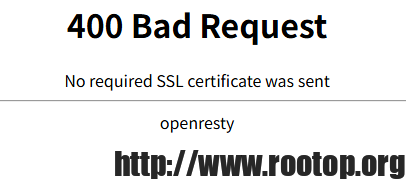
如果不导入证书,则访问时nginx会报下面错误
原创文章,转载请注明。本文链接地址: https://www.rootop.org/pages/5569.html
